S4x Industrial Security CTF
The S4x conference is “the largest gathering of ICS security talent in the world” and hosted 532 attendees from 27 countries in Miami South Beach, Florida from January 14-17th, 2019.
My buddies (Grant Foudree and Adam Crosser) and I were granted free tickets to compete as a university team (for Iowa State) in their capture-the-flag (CTF) competition.
Several months later, after all the hotels and flights were booked, we flew down to sunny Miami South Beach. We didn’t know what we were more excited for: the CTF, or the fact that the temperatures outside would be nearly three to four times warmer than back home.
We showed up on Sunday evening, thinking the conference began on Monday, but realized that it was only for the “OnRamp” training session the con holds each year, and we did not have the tickets for that event. This allowed us to spend time at the beach as well as configure our laptops for the CTF ahead. No complaints here.
Refreshed and ready to compete, we arrived at 8:58AM on Tuesday to begin the CTF. We walked up several flights of stairs and found a sign on a table with our team name on it: Cyclones. We were surrounded by tables of other CTF teams. There was a CTF staff member nearby to answer questions we had about the environment.
The CTF organizers decided to use the open-source CTFd platform to run the competition. We created a shared team account and began looking around at the challenges. Some categories included: Network, PI (for OSISoft PI, a tool used heavily in the ICS world), and Forensics/Analysis (among others I cannot remember). Unfortunately, the first day was laden with network outages and very slow speeds even to the interal CTF boxes. This made recon, attack, and research very difficult. There were points where we were waiting up to a half-hour to submit a flag. However, the CTF organizers were aware of the speed issue and worked feverishly to solve it. Near the end of the first day, the network had been stabilized and worked without a hitch.
By the end of day one, we had captured six flags. We left after the venue closed to head back to the hotel for some dinner and to continue hammering on the remote challenges.
Day two featured a fully functioning network and more progress was made across the board, including a 500 point flag capture. The venue closed around 1PM as the con had an outside event at another hotel for socialization and some physical challenges. We ate lunch and looked around quickly, but did not find any of the physical challenges we were hearing about. We continued to work on some of the remote challenges.
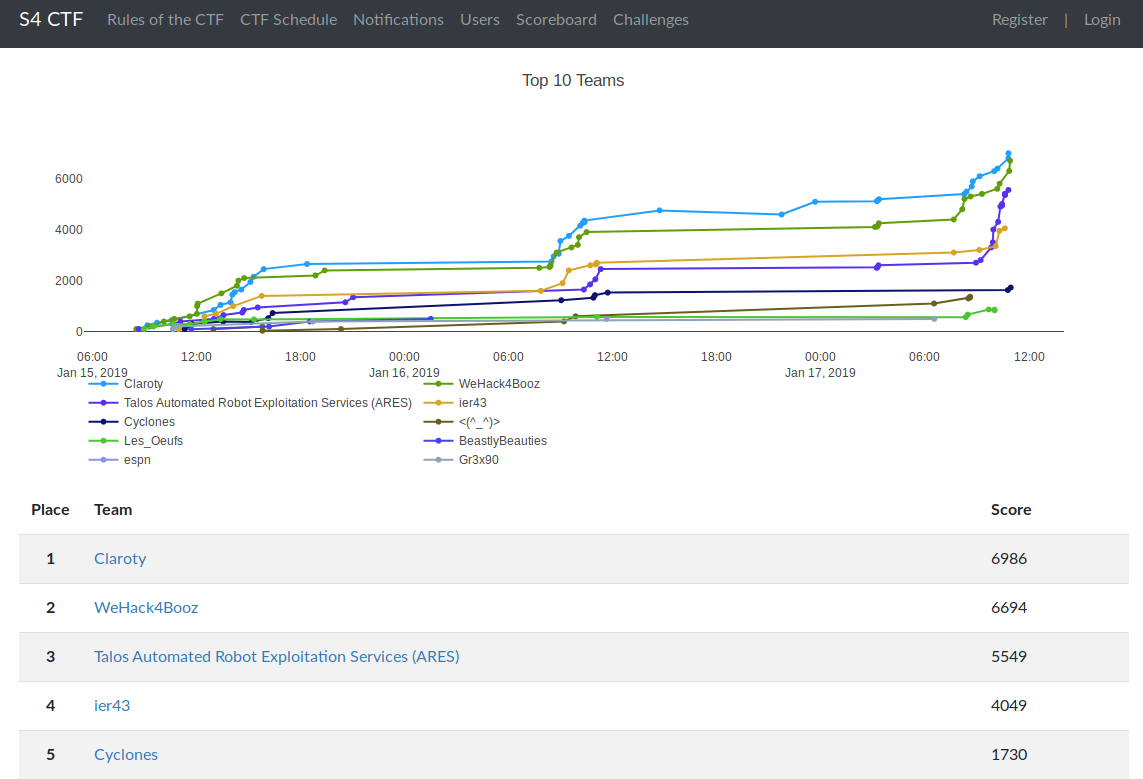
Finally, day three involved two flag captures, leading right up to the closing bell at 12:00PM. We ended up in fifth place behind corporate ICS security teams.
Interesting MySQL Challenge
There was a Windows box on one of the corporate networks. It had an IIS server and MySQL (among other things) as services on the box. I threw Nikto and Dirb at it to enumerate directories and any glaring vulnerabilities.
Nikto mentioned that PHPMyAdmin was set up on the box. I jumped over to the PHPMyAdmin panel and began poking around. When I realized the site did not require any authentication, I figured the flag would be easy to capture.
The challenge said we had to pull the flag from the Desktop. It did not say
which user. Since this was PHP, and I confirmed I had read AND write access to
the MySQL service, all I figured I had to do was use OUTFILE to write a
PHP reverse shell into a web directory and I would be in. However, there’s
a MySQL option called secure-file-priv that was set to NULL. This prevented
OUTFILE from being executed. Then I thought if I couldn’t write to a file,
surely I could read a file in. I knew the flag was on the Desktop, but I did
not know which user it was - and I needed that to specify the full path.
If I determined the full path of the desktop, perhaps the flag would simply
be named flag.txt and I could just read the flag into a table. I ran
SHOW VARIABLES WHERE Variable_Name LIKE "%dir" and a temporary data directory
popped up under a username on the box. I plugged that user’s name into a
full path for the desktop and tried to LOAD DATA INFILE. MySQL returned an
error AGAIN for secure-file-priv. Damn.
I kept researching this. I knew there had to be a way. I came across the
LOCAL keyword which allows MySQL clients to specify that the file be
read in from the client and not the server. However, with web applications
like PHPMyAdmin, the client IS the web application server, or at least MySQL
treats it that way. See this page
for more.
After appending LOCAL into LOAD DATA LOCAL INFILE..., I received the wonderful
message below.
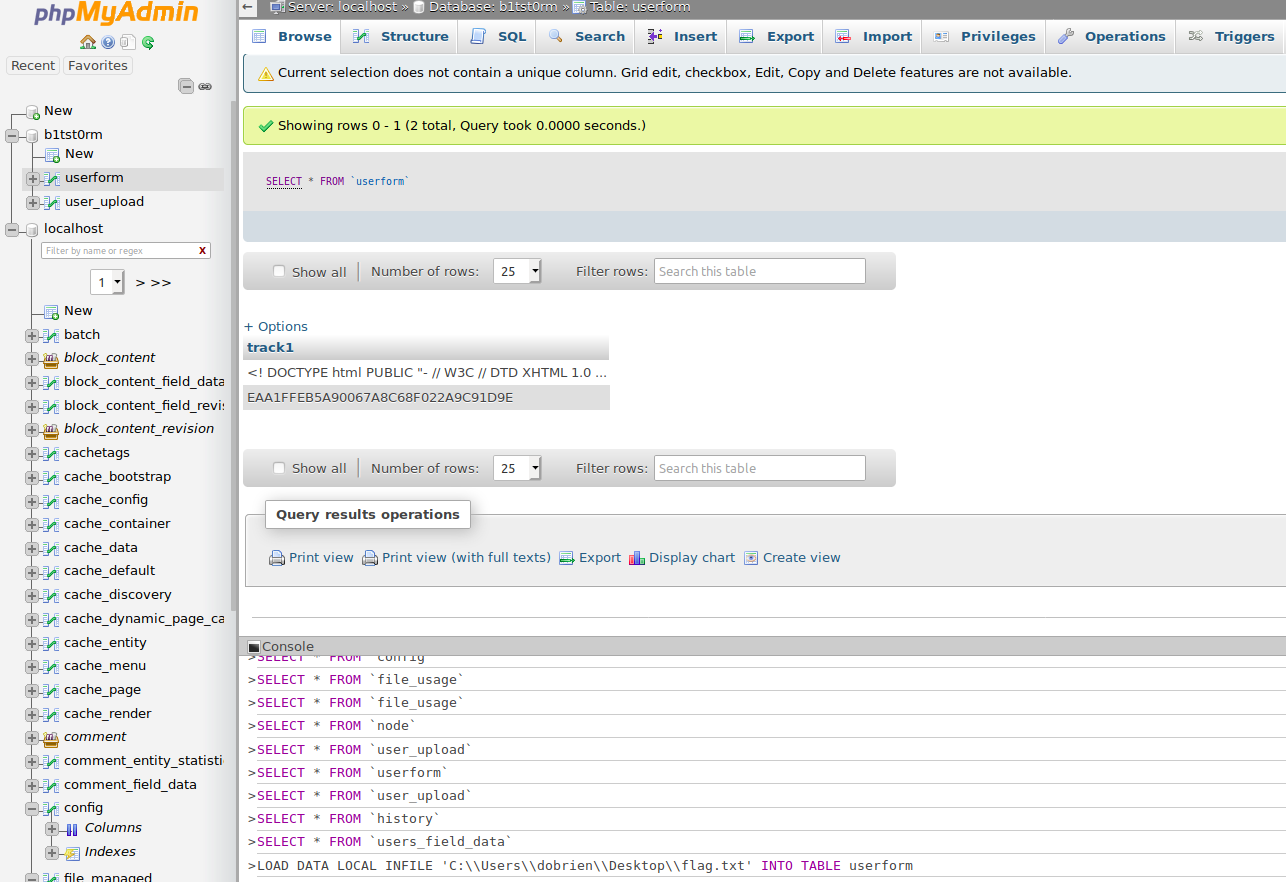
This loaded the flag into a table I created and I was able to submit for points.
What we liked
The location of the CTF was away from all of the buzz of the talks. This allowed the competitors to focus on their work, so we appreciated that.
The food and drink during the day kept us in place and was convenient for us.
The CTF had a wide array of categories and challenges.
CTFd is a solid platform to run a CTF on.
Suggestions for the future
It is always a struggle when you have network boxes that each CTF team has to attack. This often required us visiting the CTF organizers to have them “reset” the boxes after another team interruped its functionality to capture a flag. Our suggestion here would be to have less reliance on vulnerabilities or exploits that require damaging the system to capture a flag.
Also, network boxes were shut off at night. This did not leave a lot of challenges for us to work on once the venue closed at 5PM. More offline challenges in the future would be appreciated, and it would keep up the intensity of the CTF.
If offline challenges are impossible, it would be awesome to have VPN access to the network challenges.
The network challenges were all on four /16 ranges. We were not given the IP address of the boxes to attack and were simply told to “find them.” This is fine, however we believe a /24 would have been more suitable for hosting the VMs on. We were wasting time waiting for NMAP scans to complete when we could have been capturing flags. :)
Conclusion
The event was an absolute blast. We met folks from around the world, including one from our area of Des Moines, Iowa! There is a whole other world of security in the ICS space, and we were glad we could be exposed to it during this conference. Hopefully one day we’ll be back to join the hackers on the beach.
